The Google official app store has around 3 million apps to serve Android users. While all the apps are developed for helping the customers, some may be designed with ill concepts as well. Google tries its best to keep such apps from the store. However, it is not possible to keep the number of such malware to zero. On Thursday, Dr. Web, a platform focused on antivirus development, investigated and found out apps stealing Facebook details. Out of the 10 apps, 9 were available on Google Play Store.
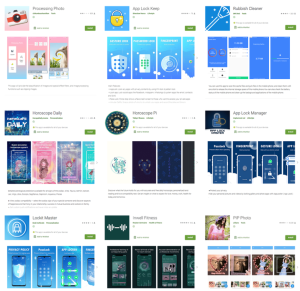
List of the trojan apps
| Applications | Developer | No. of downloads |
| App Lock Keep | Sheralaw Rence | 50K+ |
| App Lock Manager | Implummet col | 10 |
| Lockit Master | Enali mchicolo | 5K+ |
| Processing Photo | chikumburahamilton | 500K+ |
| Rubbish Cleaner | SNT.rbcl | 100K+ |
| Horoscope Daily | HscopeDaily | 100K+ |
| Horoscope Pi | Talleyr Shauna | 1k+ |
| Inwell Fitness | Reuben Germaine | 100k+ |
| PIP Photo | Lillian’s | 5M+ |
| EditorPhotoPip (removed earlier) | – | – |
The experts at Dr. Web immediately notified Google after the identification of the malicious activities. And the tech giant was quick to remove all the listed apps.
Only PIP Photo used the new cross-platform Flutter unlike all other apps based on native frameworks. The attackers made use of similar file formats and JavaScript in all of these apps for stealing Facebook login details.
How the apps tricked users into giving out Facebook credentials?
To gain the user’s trust, the applications stood out by providing the advertised services. Meanwhile, the platforms displayed ads which is very annoying for the users as it blocks the app usage for a few seconds. We all have waited five seconds on YouTube to resume the video. And many users desire to run ad-free apps. These platforms used this to their advantage and prompted users to log into Facebook for ad-free usage. It is a common practice to expand the consumer base. However, some of this software deliberately embedded ads to force users to link the Facebook account.
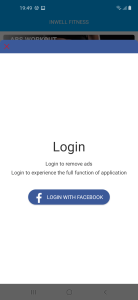
The Facebook login form was indeed authentic. But the developers tuned the trojan settings to manipulate the legitimate web page. As soon as the form was launched via WebView, these settings will direct the C&C server to load the JavaScript into the same login page. And when the user inputs id and password, it would be sent to the application ultimately reaching the C&C server. Command and control servers (C&C) are the computers run by attackers to send commands to trojan applications and retrieve stolen information. With the available settings, the attackers could thieve login credentials of other services as well.
As far as the originality of the attackers is concerned, EditorPhotoPip has a feature that could display the log data in Chinese which may hint at its origin. Google removed this platform prior to the current investigation. However, the installation files could be found on the websites.
A message to the users
If you have ever installed any of the apps mentioned above, you should change the passwords without any delay. Moreover, the users should not download random programs from untrusted sources and stick to the restriction of the Android policy. even the apps on the Google store may be malicious, so make sure to check out the user reviews and ratings before downloads. Furthermore, do not grant access to apps unless the app is safe.
Nowadays, most apps and websites require links to either Facebook or Gmail. So, the users need to verify the authenticity of such requests before proceeding.
Also read: How to counter ransomware attacks?









